Overview
From a software analysis perspective, network sniffing and MITM proxies can uncover several types of software issues:
| Weakness | Impact | Detection | Attack Vector |
|---|---|---|---|
| Lack of use of a secure channel (HTTPS) | Evilgrade, Content Modification, Privacy, etc. | Passive sniffing | Observation or manipulation of traffic on same network |
| Improper certificate chain validation | Evilgrade, Content Modification, Privacy, etc. | MITM SSL proxy | MITM (ARP spoofing, Rogue AP, etc.) |
| Sensitive info sent over proper https | Privacy | MITM SSL proxy with Root CA certificate installed | None |
CERT Tapioca can test all three of these scenarios.
Getting started
First, get the CERT Tapioca OVA. This is a standardized format that is supported by most virtualization products.
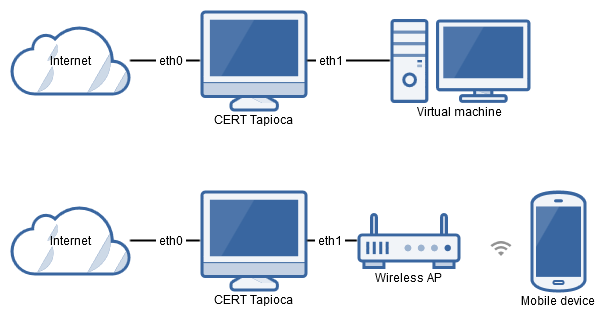
Once imported into your virtualization software of choice, it is a good idea to make a snapshot of the virtual machine before making any changes. The CERT Tapioca virtual machine has two ethernet adapters. eth0 is the WAN side, which should be connected to the internet. eth1 is the LAN side, which should be connected to the application to test. This could be a virtual network for connecting to other virtual machines, or this can be bridged to a physical network. For example, bridging eth1 to a wireless network adapter can allow testing of applications on a physical device that has WiFi capabilities.
For VMware products, eth0 appears to match up with the first listed network adapter. For VirtualBox, it appears that eth0 matches up with the second network adapter listed in the virtual machine configuration. Either way, be sure that the internet connection is configured to connect to the eth0 adapter.