...
- Log in to VINCE.
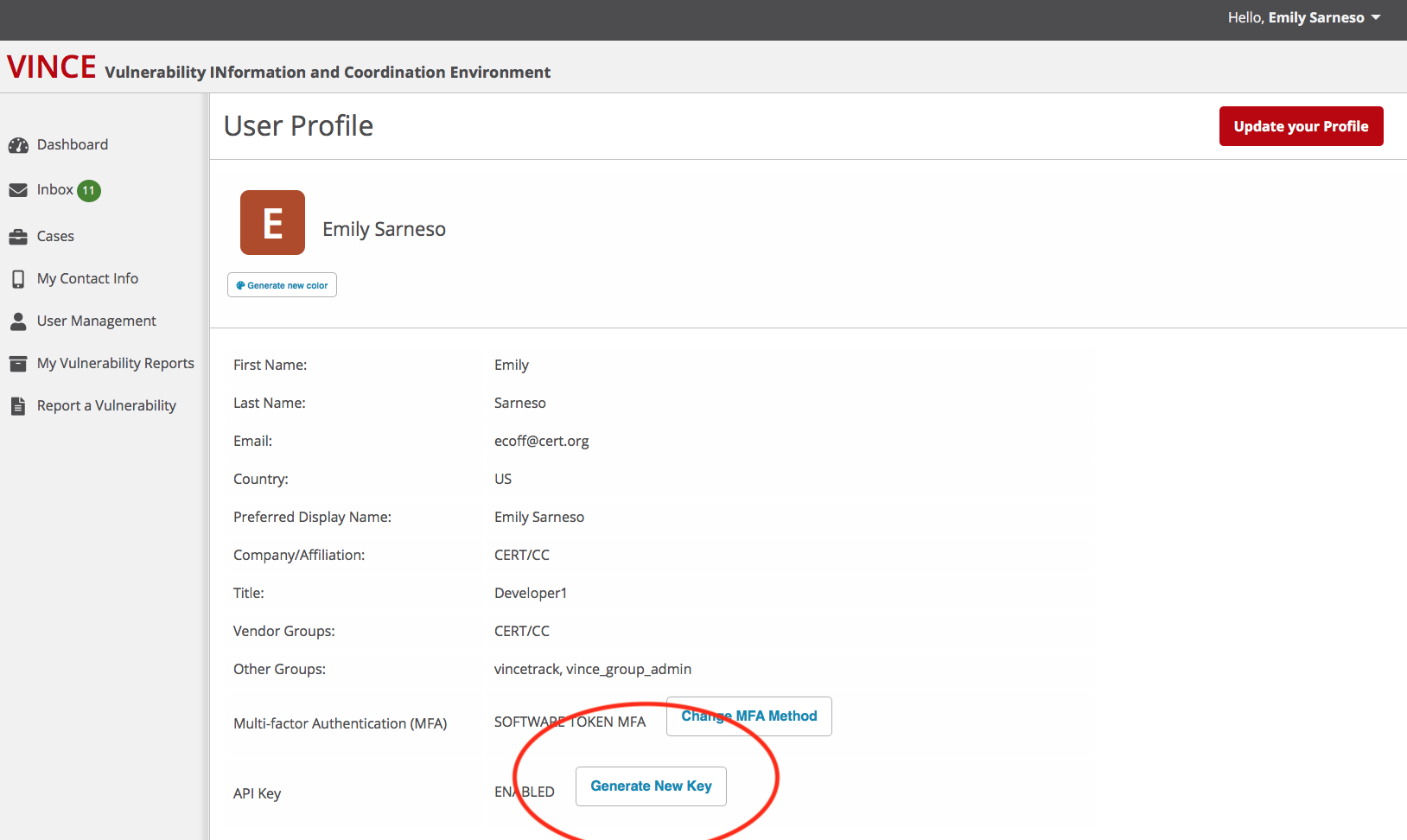
- Go to your User Profile.
- Scroll down to "Generate API Key".
- Copy they API key to a safe place, you will not be able to access it again. If lost, you need to regenerate a new one.
- Use the API key in the headers of your request as shown below.
| Code Block | ||
|---|---|---|
| ||
headers={'Authorization': "Token {}".format(token)} |
...
| Code Block | ||
|---|---|---|
| ||
#API: /vince/comm/api/case/710582/note/ # get draft vul note
{ 'content': '### Overview\r\n'
'\r\n'
'Testing API so need some content.\r\n'
'\r\n'
'\r\n'
'### Description\r\n'
'\r\n'
'### Impact\r\n'
'The complete impact of this vulnerability is not yet known.\r\n'
'\r\n'
'### Solution\r\n'
'The CERT/CC is currently unaware of a practical solution to '
'this problem.\r\n'
'\r\n'
'### Acknowledgements\r\n'
'Thanks to the reporter who wishes to remain anonymous.\r\n'
'\r\n'
'This document was written by Emily Sarneso.',
'datefirstpublished': None,
'dateupdated': '2020-11-17T19:13:07.755453Z',
'published': False,
'references': ['www.example.org', 'www.example.com'],
'revision': 2,
'title': 'test',
'vuid': '785701'} |
...
Get Vulnerability Advisory in CSAF format
| Code Block | ||
|---|---|---|
| ||
#update vendor status# get the vulnerability note, if available api = f'https://kb.cert.org/vince/comm/api/case/{case}495801/vendorcsaf/statement/' data headers= [{'vendorcontent-type':'application/json', 'Authorization': "Token {}".format(token) } r = requests.get(api, headers=headers, stream=True) print(r.text) |
| Code Block | ||
|---|---|---|
| ||
#API: /vince/comm/api/case/495801/csaf/ # get draft vul note {
"document": {
"acknowledgments": [
{
"urls": [
"https://kb.cert.org/vuls/id/495801#acknowledgements"
]
}
],
"category": "CERT/CC Vulnerability Note",
"csaf_version": "2.0",
"notes": [
{
"category": "summary",
"text": "### Overview\r\n\r\nVersions 1.1.5 and earlier of the mu HTTP deamon ......",
"title": "Summary"
}
],
"publisher": {
"category": "coordinator",
"contact_details": "Email: cert@cert.org, Phone: +1412 268 5800",
"issuing_authority": "CERT/CC under DHS/CISA https://www.cisa.gov/cybersecurity also see https://kb.cert.org/ ",
"name": "CERT/CC",
"namespace": "https://kb.cert.org/"
},
"references": [
{
"url": "https://vuls.cert.org/confluence/display/Wiki/Vulnerability+Disclosure+Policy",
"summary": "CERT/CC vulnerability disclosure policy"
},
{
"summary": "CERT/CC document released",
"category": "self",
"url": "https://kb.cert.org/vuls/id/495801"
},
{
"url": "https://derekabdine.com/blog/2022-arris-advisory",
"summary": "https://derekabdine.com/blog/2022-arris-advisory"
},
{
"url": "https://www.cisa.gov/uscert/ncas/tips/ST15-002",
"summary": "https://www.cisa.gov/uscert/ncas/tips/ST15-002"
}
],
"title": "muhttpd versions 1.1.5 and earlier are vulnerable to path traversal",
"tracking": {
"current_release_date": "2022-08-05 20:02:52.605648+00:00",
"generator": {
"engine": {
"name": "VINCE",
"version": "1.50.3"
}
},
"id": "VU#495801",
"initial_release_date": "2022-08-04 18:22:24.069865+00:00",
"revision_history": [
{
"date": "2022-08-05 20:02:52.605648+00:00",
"number": "1.20220805200252.2",
"summary": "Released on 2022-08-05 20:02:52.605648+00:00"
}
],
"status": "final",
"version": "1.20220805200252.2"
}
},
"vulnerabilities": [
{
"title": "The base firmware for this modem contains an MIT-licensed web server from an individual developer called \"muhttpd.",
"notes": [
{
"category": "summary",
"text": "The base firmware for this modem contains an MIT-licensed web server from an individual developer called \"muhttpd.\" This server has been unmaintained since 2010. The server has a path traversal vulnerability that allows any file on the modem to be read as root"
}
],
"cve": "CVE-2022-31793",
"ids": [
{
"system_name": "CERT/CC V Identifier ",
"text": "VU#495801"
}
],
"product_status": {
"known_not_affected": [
"CSAFPID-eb07f774-32d4-11ed-aeca-0aa659cdc35f"
]
}
}
],
"product_tree": {
"branches": [
{
"category": "vendor",
"name": "AT&T",
"product": {
"name": "AT&T Products",
"product_id": "CSAFPID-eb07f774-32d4-11ed-aeca-0aa659cdc35f"
}
},
{
"category": "vendor",
"name": "SaskTel",
"product": {
"name": "SaskTel Products",
"product_id": "CSAFPID-eb082dc0-32d4-11ed-aeca-0aa659cdc35f"
}
}
]
}
} |
Update vendor status
| Code Block | ||
|---|---|---|
| ||
#update vendor status api = f'https://kb.cert.org/vince/comm/api/case/{case}/vendor/statement/' data = [{'vendor': 3548, 'status':'Not Affected', 'references':["http://www.test.gov", "https://www. 3548, 'status':'Not Affected', 'references':["http://www.test.gov", "https://www.google.com"], 'share':True, 'vulnerability':'CVE-2020-19293', 'statement': 'This is my statement'}, {'vendor': 3548, 'status':'Affected', 'statement':"Test", 'references':["http://www.test.gov","https://www.google.com"], 'share':True, 'vulnerability':'VU#785701.2'}] r = requests.post(api, headers=headers, data=json.dumps(data)) print(r.text) |
...
| Code Block |
|---|
# lookup CVE-2021-55555 - must have access to case otherwise 404 api = f'https://kb.cert.org/vince/comm/api/vuls/cve/20212020-5555519293/' headers={'content-type':'application/json', 'Authorization': "Token {}".format(token) } r = requests.get(api, headers=headers, stream=True) print(r.text) |
...